In the ever-expanding digital ecosystem, the need for cybersecurity frameworks has become increasingly evident as they provide structured approaches to address the growing complexity of cyber threats. Two of the most commonly used frameworks are the NIST Cybersecurity Framework (CSF) and the NIST Risk Management Framework (RMF).

NIST Cybersecurity Framework
NIST’s CSF is a comprehensive set of guidelines and best practices designed to enhance cybersecurity across various industries. It was designed to be flexible and adaptable for various use cases. The CSF consists of three sections: the framework core, the framework implementation tiers, and the framework profiles.
The framework core is made up of five core components:
- Identify: This initial step involves understanding and managing the cybersecurity risks specific to your organization. It includes identifying and prioritizing assets, assessing vulnerabilities, and understanding the potential impact of cyber threats.
- Protect: The Protect component focuses on implementing safeguards to reduce the risk of a cybersecurity incident. This includes the development of access controls, encryption, and security policies that can protect your organization’s assets.
- Detect: Detecting cyber threats in a timely manner is crucial to minimizing damage. This component involves implementing measures to identify cybersecurity events, whether through automated systems or human monitoring, as well as establishing incident response plans.
- Respond: In the event of a cybersecurity incident, the ability to respond effectively is vital. This component covers response planning, communication, and mitigation strategies to address and recover from cybersecurity events.
- Recover: The final component deals with the recovery process after a cybersecurity incident. It includes strategies for maintaining resilience, restoring affected systems, and learning from the incident to prevent future occurrences.
Note that the CSF should not be read as a playbook or a series of steps. Each component requires individual consideration. Here are a couple examples of considerations for each component:
- Identify:
- An organization must identify its valuable data in order to secure it.
- Regularly identifying vulnerabilities so they may be protected.
- Protect:
- Provide regular backups to your data so it is protected from ransomware.
- Patch vulnerabilities so that they cannot be exploited.
- Detect:
- Understand the expected data flow of the organization.
- Develop intrusion detection processes.
- Respond:
- Develop and test your incident response plans ahead of time.
- Learn how to coordinate with stakeholders.
- Recover:
- Return to regular operations after an attack.
- Manage public relations and company reputation.
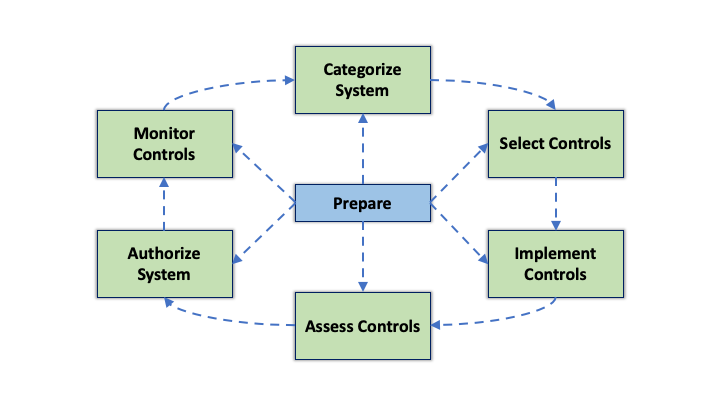
NIST Risk Management Framework
Unlike the CSF, the RMF is a step-by-step guide and its purpose is to provide a flexible process for integrating cybersecurity and privacy into a system’s development life cycle. The seven steps of the RMF are as follows:
- Prepare: In the Prepare step, an organization should define the context of the RMF and carry out essential activities to prepare subsequent RMF steps. This includes facilitating communication between senior leaders and executives, identifying, prioritizing and focusing resources, and reducing complexity of the information technology infrastructure.
- Categorize: In this step, an organization categorizes its systems and information by importance and confidentiality. Consider the adverse affects of an attack with respect to the CIA triad.
- Select: The Select step references SP 800-53, a NIST document that provides guidelines on controls. In this step, an organization selects and tailors the controls necessary to protect the organization.
- Implement: Implement the previously selected controls and document how those controls are deployed.
- Assess:
- Authorize:
- Monitor: